Key Takeaways: Critical Cybersecurity Threats for 2026
- AI-powered cyber attacks will become significantly more sophisticated, with deepfakes and autonomous malware posing unprecedented threats to business operations and data security.
- Ransomware will evolve beyond simple encryption to incorporate multiple extortion techniques, targeting critical infrastructure with increasing precision.
- Supply chain vulnerabilities will reach critical mass as attackers exploit third-party software, hardware components, and cloud provider security gaps.
- Quantum computing developments are accelerating, potentially rendering current encryption methods obsolete faster than organizations can implement post-quantum cryptography.
- Zero Trust Architecture and AI-driven security tools will become essential defensive measures rather than optional security enhancements.

“What Is Cybersecurity? – Forage” from www.theforage.com and used with no modifications.
The cybersecurity landscape is rapidly transforming as we approach 2026, with threat actors leveraging cutting-edge technologies to develop more sophisticated, persistent, and devastating attacks. Organizations face an increasingly complex digital battlefield where traditional security approaches are becoming obsolete. The convergence of artificial intelligence, quantum computing advancements, and expanding digital ecosystems is creating perfect conditions for novel attack vectors that many businesses are ill-prepared to counter.
For cybersecurity professionals and business leaders, understanding these emerging threats isn’t just an academic exercise—it’s an essential component of organizational resilience and business continuity. With attack surfaces expanding and threat actors growing more sophisticated, the coming years demand a fundamental shift in security strategies and investments.
AI-Powered Cyber Attacks: The New Digital Battlefield

“Demand Cybersecurity Jobs …” from nyscas.touro.edu and used with no modifications.
Artificial intelligence has revolutionized numerous industries, but its application in cybersecurity presents a double-edged sword. While AI strengthens defensive capabilities, it also empowers attackers with unprecedented tools to automate, scale, and enhance their operations. By 2026, AI-driven attacks will have evolved from experimental concepts to mainstream threats, with attackers leveraging machine learning to create adaptive malware that evades traditional detection methods.
How Criminals Use AI to Automate Sophisticated Attacks
The cybercriminal ecosystem is rapidly adopting AI to automate attack processes that once required significant human intervention. Advanced machine learning models now enable attackers to conduct reconnaissance at scale, identifying vulnerabilities across vast networks with minimal human oversight. These AI systems can analyze enormous datasets of security practices and defensive measures, identifying patterns and weaknesses that human attackers might overlook.
Particularly concerning is the emergence of autonomous malware capable of making operational decisions without command-and-control instructions. These self-directing threats can adapt to defensive measures in real-time, modifying their attack patterns and evasion techniques based on the security environment they encounter. By 2026, security researchers anticipate widespread deployment of malware that can intelligently prioritize targets based on potential value, adjust attack vectors when blocked, and even determine optimal times for attack execution to minimize detection.
The automation capabilities extend to vulnerability discovery as well, with AI systems scanning code and systems for zero-day vulnerabilities at unprecedented speeds. This technological evolution dramatically reduces the time between vulnerability discovery and exploitation, creating a narrower window for organizations to implement patches and countermeasures.
Deepfake Technology in Business Fraud and Social Engineering
Deepfake technology represents one of the most alarming AI applications in the cybersecurity threat landscape for 2026. As voice synthesis and video manipulation technologies continue to improve, the ability to create convincing impersonations of executives and trusted figures has reached disturbing levels of realism. These synthetic media tools enable highly targeted social engineering attacks that bypass traditional security awareness training.
Business email compromise (BEC) attacks will evolve into business presence compromise, where attackers don’t just spoof emails but create convincing video conference calls, voice messages, and other digital communications that appear to come from legitimate executives. Financial departments will face increasingly convincing requests for fund transfers or sensitive information from what appear to be trusted sources. The challenge of distinguishing genuine communications from sophisticated fakes will place enormous pressure on verification protocols and human judgment.
“By 2026, we expect to see at least five major public cases where deepfake technology was used to facilitate fraud exceeding $10 million per incident. Organizations without multi-factor verification protocols for financial transactions will be particularly vulnerable.” – Cloud Security Alliance, Emerging Threats Report
AI-Generated Phishing: Why Detection Just Got Harder
The days of easily spotted phishing attempts with obvious grammatical errors and suspicious formatting are rapidly disappearing. AI-powered phishing campaigns utilize natural language processing models to create contextually aware, grammatically perfect communications tailored to specific targets. These systems analyze social media profiles, professional networks, and even writing styles to craft messages that precisely mimic legitimate communications from trusted sources.
What makes these attacks particularly effective is their personalization capabilities. Rather than broad-spectrum phishing campaigns, AI enables highly targeted spear-phishing that incorporates recipient-specific details gathered from data aggregation. These attacks reference real projects, use appropriate industry terminology, and mirror communication patterns of legitimate contacts. The contextual relevance makes traditional “red flags” much harder to spot, even for security-conscious employees.
By 2026, these AI-generated phishing attacks will incorporate real-time adaptive elements, modifying their approach based on user responses and interaction patterns. This dynamic targeting represents a significant evolution from current static phishing techniques and will require equally sophisticated AI-powered detection systems to counter effectively.
Ransomware Evolution: Beyond Simple Encryption

“Ransomware Is ‘More Brutal’ Than Ever …” from www.wired.com and used with no modifications.
The ransomware landscape of 2026 bears little resemblance to its predecessors. What began as straightforward encryption-for-ransom schemes has evolved into sophisticated, multi-faceted operations with devastating consequences for unprepared organizations. Threat actors have significantly refined their targeting capabilities, attack methodologies, and monetization techniques, creating ransomware variants that specifically exploit industry-specific vulnerabilities and processes.
This evolution represents a fundamental shift from opportunistic attacks to strategic campaigns designed to maximize leverage over victims and ensure payment. The technical sophistication of these attacks has increased exponentially, with ransomware groups now employing legitimate penetration testing tools, living-off-the-land techniques, and advanced persistence mechanisms that make detection extraordinarily difficult even for well-defended networks.
Double and Triple Extortion Tactics
Traditional ransomware attacks focused solely on encrypting data and demanding payment for decryption keys. By 2026, multi-layered extortion has become standard practice, with attackers employing combinations of data encryption, data exfiltration, and additional pressure tactics. In these sophisticated campaigns, victims face not only the immediate operational disruption of encrypted systems but also the threat of sensitive data publication, regulatory penalties, and reputational damage.
Triple extortion has emerged as particularly effective, adding distributed denial-of-service attacks against critical systems or direct pressure on customers and partners as a third layer of coercion. Some ransomware groups have even begun targeting investors and board members with personalized threats, leveraging stolen corporate data to increase pressure for payment. These tactics significantly complicate incident response decisions, as even organizations with robust backup systems face multiple vectors of potential damage.
Critical Infrastructure Targeting
The targeting of critical infrastructure represents one of the most concerning developments in the ransomware landscape. Sophisticated threat actors have developed industry-specific attack modules designed to target operational technology environments in sectors including healthcare, energy, transportation, and water treatment. These attacks specifically target vulnerabilities in industrial control systems, supervisory control and data acquisition (SCADA) networks, and other critical operational components.
Unlike traditional IT-focused ransomware, these specialized variants are designed to maximize physical disruption and safety concerns, creating unprecedented leverage over victims. The potential for ransomware to impact physical systems—from power distribution networks to medical devices—has elevated these attacks from financial crimes to potential national security concerns. Government agencies worldwide have responded with more aggressive intervention, but the sophisticated nature of these attacks makes prevention challenging even with heightened scrutiny.
“Ransomware targeting critical infrastructure now accounts for 43% of all major ransomware incidents, with healthcare, energy, and municipal services experiencing the highest growth in targeted attacks. Average downtime in these incidents has increased to 16 days, with recovery costs averaging $8.7 million per incident.” – National Cybersecurity Center, Critical Infrastructure Threat Report 2025
Ransomware-as-a-Service (RaaS) Expansion
The ransomware ecosystem has matured into a sophisticated service-based model that dramatically lowers barriers to entry for would-be attackers. Professional ransomware development teams now operate sophisticated affiliate programs, providing access to enterprise-grade malicious code, infrastructure, and support services in exchange for a percentage of ransom payments. These RaaS operations function with corporate-like efficiency, offering user-friendly control panels, technical support, and even guaranteed results to their criminal customers.
By 2026, these services have expanded to include specialized modules for specific industries, automated negotiation systems, and comprehensive victim profiling tools that help determine optimal ransom demands. The professionalization of ransomware operations has created a troubling acceleration in attack frequency and sophistication, with some RaaS providers even offering “bronze, silver, and gold” service tiers with increasingly advanced features and support options.
Supply Chain Vulnerabilities Reach Critical Mass

“Supply Chain Security Using NIST CSF 2.0” from www.cm-alliance.com and used with no modifications.
Supply chain attacks have emerged as one of the most devastating attack vectors, allowing threat actors to compromise thousands of organizations through a single point of failure. By targeting software providers, hardware manufacturers, and managed service providers, attackers gain unprecedented scale and access to organizations that may otherwise maintain robust security practices. These attacks exploit the implicit trust organizations place in vendors and third-party code, turning trusted relationships into security liabilities.
The sophistication of supply chain attacks has increased dramatically, with threat actors dedicating significant resources to understanding complex software build processes, hardware manufacturing workflows, and cloud service architectures. By 2026, the frequency and impact of these attacks have forced a fundamental reconsideration of third-party risk management practices across industries, with organizations implementing zero-trust approaches even for long-established vendor relationships.
Third-Party Software Risks
Software supply chain compromises represent a particularly insidious threat due to the complexity of modern application development practices. With organizations relying on hundreds or thousands of third-party components, libraries, and frameworks, the attack surface has expanded enormously. Sophisticated threat actors now target popular open-source components, development tools, and code repositories, inserting malicious code that propagates downstream to countless organizations.
The 2026 landscape has seen these attacks become increasingly subtle, with malicious code designed to activate only under specific conditions or after extended dormant periods. This selective execution makes detection extraordinarily difficult, as traditional testing may never trigger the malicious functionality. The compromise of continuous integration/continuous deployment (CI/CD) pipelines has emerged as a particularly effective technique, allowing attackers to inject malicious components during the build process while leaving source code repositories untouched.
Dependency confusion attacks have also evolved significantly, with attackers exploiting complex package management systems to insert malicious components that are preferentially selected over legitimate libraries. These attacks take advantage of inconsistencies in how development environments resolve dependencies, often bypassing security controls that focus exclusively on known vulnerable components rather than potentially malicious ones.
Hardware Supply Chain Compromises
Hardware supply chain attacks have reached new levels of sophistication, with state-sponsored threat actors leading efforts to compromise physical components during manufacturing or distribution. These attacks target everything from server motherboards to network equipment, introducing hardware-level backdoors that remain invisible to most security scanning tools. The persistence and stealth of hardware-level compromises make them particularly valuable for long-term intelligence gathering and strategic advantage.
The globalized nature of hardware manufacturing creates numerous intervention points for sophisticated attackers, from component sourcing to assembly and distribution. By 2026, concerns about hardware supply chain integrity have forced many organizations to implement rigorous hardware verification processes, including comprehensive component testing and tamper-evident packaging requirements. Despite these precautions, the complexity of modern hardware makes absolute verification nearly impossible, creating an enduring vulnerability that sophisticated attackers continue to exploit.
| Hardware Component | Attack Vector | Detection Difficulty | Potential Impact |
|---|---|---|---|
| Network Interface Cards | Modified firmware with covert communication capabilities | Extremely High | Persistent data exfiltration channel |
| Server Motherboards | Implanted microcontrollers or modified chipsets | Very High | Administrative access regardless of OS security |
| Storage Devices | Hidden partitions with malicious code | High | Persistent malware reinstallation |
| Peripherals (Cameras, Keyboards) | Modified firmware for keystroke capture or surveillance | Medium | Credential theft, physical surveillance |
Cloud Provider Security Gaps
As organizations increasingly migrate critical workloads to cloud environments, the security boundaries of corporate networks have become increasingly abstract and complex to defend. By 2026, sophisticated attackers have shifted significant resources toward compromising cloud service providers and managed service providers, recognizing the enormous leverage these targets provide. A successful compromise of a major cloud provider can potentially expose thousands of customer environments, making these attacks extraordinarily high-value targets for both criminal and nation-state actors.
The complexity of cloud service models—spanning infrastructure, platform, and software services—creates numerous potential security gaps at the boundaries between provider and customer responsibility. Configuration errors, API vulnerabilities, and identity management weaknesses at these intersection points have become primary attack vectors. The rapid pace of feature development in cloud environments also creates continuous change in security models, requiring constant vigilance and expertise that many organizations struggle to maintain.
Shared resource vulnerabilities have emerged as particularly concerning in multi-tenant cloud environments, with sophisticated attackers developing techniques to bypass virtualization boundaries and access data from other customers. These side-channel attacks exploit fundamental architectural characteristics of cloud computing, making them extremely difficult to fully mitigate without significant performance impacts or architectural changes.
Quantum Computing Threats to Cryptographic Systems

“What Is Quantum Cryptography? A Look at …” from thequantuminsider.com and used with no modifications.
The race toward practical quantum computing represents one of the most significant threats to current cybersecurity infrastructure. Unlike incremental improvements in traditional attack techniques, quantum computing poses an existential threat to the cryptographic foundations that secure virtually all digital systems. The mathematical problems that make current encryption secure—particularly public key cryptography—become trivially solvable with sufficient quantum computing power, potentially rendering decades of security infrastructure obsolete.
Why Current Encryption Standards Are at Risk
The security of most encryption systems relies on mathematical problems that are computationally infeasible to solve with classical computers. Public key cryptography, which secures everything from financial transactions to encrypted communications, depends primarily on the difficulty of factoring large prime numbers or solving discrete logarithm problems. Quantum computers, leveraging algorithms like Shor’s algorithm, can theoretically solve these problems exponentially faster than classical computers, effectively breaking these cryptographic systems.
RSA, ECC, and other widely deployed public key cryptographic standards will become vulnerable once quantum computers reach sufficient scale and stability. Organizations face the daunting challenge of identifying all vulnerable cryptographic implementations throughout their technology stacks—from VPN connections to digital certificates to secure communications channels—and developing migration strategies. This cryptographic inventory process alone represents a massive undertaking for complex organizations with decades of technology accumulation.
Even data encrypted with current standards and stored for future access faces significant risk from retrospective decryption. Sophisticated threat actors are already harvesting encrypted data with the expectation of decrypting it once quantum computing capabilities mature—a strategy known as “harvest now, decrypt later.” This means sensitive information transmitted today could be exposed in the future, even if it appears secure under current standards.
Timeline for Quantum Threat Realization
While debate continues about precisely when quantum computers will reach the capability to break current cryptographic standards, the timeline has compressed significantly. Many experts now predict that sufficiently powerful quantum computers could emerge within the next 5-10 years, creating urgency for organizations to begin cryptographic transitions immediately. The migration to quantum-resistant algorithms typically requires years to implement across complex systems, creating a potentially dangerous gap between threat emergence and organizational readiness.
The National Institute of Standards and Technology (NIST) has accelerated its process for standardizing post-quantum cryptographic algorithms, finalizing several candidates for different applications. However, implementing these new standards requires extensive testing, validation, and deployment across countless systems and applications. Organizations that delay preparations may find themselves unable to complete migrations before quantum threats materialize, creating significant security exposures across their technology portfolios.
IoT Exploitation in Corporate Environments

“How the Internet of Things (IoT) became …” from www.weforum.org and used with no modifications.
The explosive growth of Internet of Things (IoT) devices in corporate environments has created vast new attack surfaces with unique security challenges. By 2026, the average enterprise network contains tens of thousands of connected devices, many with minimal security features, limited update mechanisms, and extensive access to sensitive networks. These devices—ranging from environmental sensors to security cameras to smart building systems—often operate with persistent connectivity and privileged network access, making them ideal targets for attackers seeking initial access or lateral movement opportunities.
To understand more about the evolving digital landscape, explore what is the Metaverse and its implications for cybersecurity.
Smart Building Security Weaknesses
Modern commercial buildings have evolved into complex digital ecosystems with interconnected systems controlling everything from HVAC and lighting to physical access and occupancy monitoring. These smart building technologies offer significant operational efficiencies but introduce substantial security risks when improperly segmented from corporate networks. Attackers increasingly target these systems as a pathway into otherwise well-defended corporate environments, exploiting the frequent lack of security oversight for operational technology.
Building automation systems often run on outdated protocols with minimal authentication requirements, creating ideal conditions for unauthorized access. Once compromised, these systems can provide attackers with persistent access, opportunities for physical security bypasses, and potential platforms for disruptive attacks. The convergence of physical and digital security in modern buildings means that compromised building systems can potentially impact both domains, creating complex incident response scenarios that many organizations are ill-prepared to address.
Operational Technology (OT) Convergence Risks
The increasing convergence of traditional IT networks with operational technology used in manufacturing, utility management, and industrial control creates particularly concerning attack vectors. These OT systems—which directly control physical processes—were typically designed for reliability and safety rather than security, often lacking basic security controls like encryption, authentication, or regular patching mechanisms. As organizations connect these systems to corporate networks for efficiency and monitoring purposes, they create bridges between historically isolated environments with dramatically different security postures.
Sophisticated attackers have developed specialized tools and techniques for compromising industrial control systems once they gain access to connected networks. These attacks can potentially impact physical operations, creating safety risks, production disruptions, and environmental hazards beyond typical data security concerns. The potential consequences extend far beyond data loss or service disruption, potentially including physical damage to equipment, environmental release events, or even threats to human safety in certain industrial contexts.
Medical IoT Device Vulnerabilities
Healthcare environments face particularly acute IoT security challenges due to the proliferation of connected medical devices with direct patient safety implications. These devices—ranging from infusion pumps and patient monitors to imaging equipment and implantable devices—frequently run proprietary firmware with minimal security controls and extended operational lifespans. Many remain in service for decades with limited or no security updates, creating persistent vulnerabilities that cannot be easily mitigated.
By 2026, targeted attacks against healthcare delivery organizations increasingly focus on medical device vulnerabilities as entry points, recognizing both their security weaknesses and the extraordinary leverage they provide in ransom negotiations when patient safety is potentially impacted. Healthcare organizations face the complex challenge of securing these devices without disrupting their clinical functions or requiring wholesale replacement of expensive equipment. This tension between security requirements and operational constraints creates enduring vulnerabilities that sophisticated attackers readily exploit.
Nation-State Cyber Operations Target Private Sector
“Nation-state cyberattacks: It’s bigger …” from www.route-fifty.com and used with no modifications.
The line between government-sponsored cyber operations and private sector targets has increasingly blurred. Nation-state actors now routinely target private organizations for intelligence collection, intellectual property theft, and strategic positioning within critical infrastructure. These sophisticated threat actors bring unprecedented resources, technical capabilities, and operational patience to their campaigns, creating challenges that exceed the defensive capabilities of most private organizations.
Critical Infrastructure in the Crosshairs
Critical infrastructure sectors face intensifying targeting from nation-state actors seeking to establish persistent access for potential future operations. These advanced persistent threats maintain long-term access within compromised networks, often for years, while carefully avoiding detection. Unlike cybercriminal groups focused on immediate financial gain, these state-sponsored actors prioritize stealth and persistence, making their operations exceptionally difficult to detect with conventional security monitoring.
The potential for escalation from espionage to disruptive or destructive operations during geopolitical conflicts creates particular concern for organizations in energy, transportation, financial services, and other critical sectors. These organizations increasingly find themselves on the front lines of geopolitical tensions, facing sophisticated adversaries with capabilities traditionally associated with military operations rather than typical cybercriminal activity. The burden of defending against nation-state level threats has created challenging questions about the appropriate boundaries between private sector responsibility and government protection.
Intellectual Property Theft Campaigns
Advanced persistent threats increasingly target intellectual property across industries, with particular focus on research and development operations, proprietary manufacturing processes, and unreleased product designs. These campaigns aim to compress R&D timelines and gain competitive advantages by acquiring innovations without the associated development costs. Organizations in sectors including pharmaceuticals, aerospace, automotive, and advanced manufacturing face sophisticated attacks designed specifically to identify and extract their most valuable intellectual assets.
These targeted operations often combine technical exploitation with human intelligence operations, including sophisticated social engineering, insider recruitment, and supply chain compromises. The comprehensive nature of these campaigns makes defense particularly challenging, requiring coordination between cybersecurity, physical security, and personnel security programs. Many organizations struggle to implement holistic protection for their innovation processes while maintaining the open collaboration required for effective research and development activities.
5G and Edge Computing Security Challenges

“Enterprise Security: 5G Edge Computing …” from cadinc.com and used with no modifications.
The widespread deployment of 5G networks and edge computing architectures has dramatically transformed the cybersecurity landscape, creating both new capabilities and novel security challenges. These technologies enable unprecedented connectivity, reduce latency for critical applications, and support massive IoT deployments—but also create expanded attack surfaces, new trust boundaries, and complex multi-party security dependencies that many organizations struggle to effectively manage.
Network Slicing Security Concerns
5G network slicing—which allows operators to create multiple virtual networks on shared physical infrastructure—creates new security isolation challenges and potential cross-slice attack vectors. While slicing provides logical separation between different types of traffic and applications, vulnerabilities in the underlying orchestration and management systems could potentially allow attackers to breach these boundaries. Organizations leveraging private 5G networks for critical operations face the challenge of verifying that logical separation controls provide sufficient security isolation for sensitive functions.
The dynamic nature of network slice provisioning and management introduces additional complexity to security monitoring and assurance activities. Traditional perimeter-based security models become increasingly ineffective in these environments, requiring new approaches to security architecture that emphasize zero-trust principles, continuous validation, and security that follows workloads regardless of their physical or virtual location. Organizations implementing 5G technologies must develop new security monitoring capabilities specifically designed for virtualized network environments with dynamic resource allocation.
Distributed Processing Vulnerabilities
Edge computing architectures distribute processing capabilities closer to data sources, enabling lower latency and more efficient bandwidth utilization—but also creating new security challenges around distributed trust, credential management, and security monitoring. These distributed processing nodes often operate in physically unsecured locations with limited local security controls, creating potential for physical tampering or localized compromise that can affect the broader environment.
The deployment of sensitive processing capabilities and data storage outside traditional secured data centers creates fundamental changes in security architecture requirements. Organizations must implement sophisticated remote attestation mechanisms, secure boot processes, and encrypted processing capabilities to maintain security assurance for distributed computing resources. The complexity of securing these distributed environments frequently exceeds organizational capabilities, creating security gaps that sophisticated attackers readily exploit.
Identity-Based Attacks Bypass Traditional Security
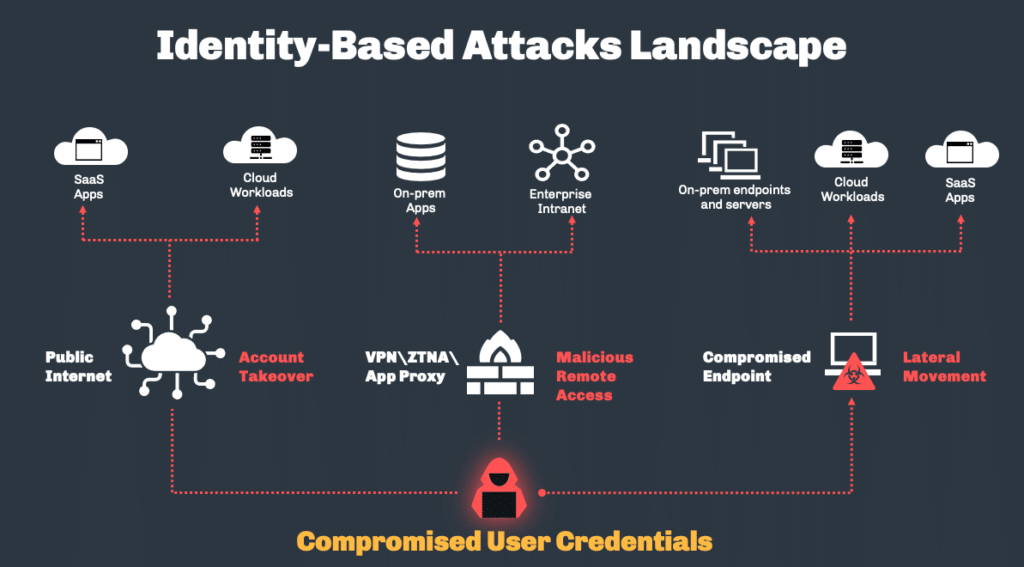
“What is an Identity-Based Attack …” from www.silverfort.com and used with no modifications.
As perimeter-based security controls have strengthened, attackers have shifted focus to identity compromise as the primary method for gaining unauthorized access. By obtaining valid credentials—whether through phishing, credential stuffing, social engineering, or other techniques—attackers can bypass traditional security controls and gain authenticated access to systems and data. These identity-based attacks have become particularly effective as organizations migrate to cloud environments where identity serves as the primary security boundary.
Credential Theft Evolution
Credential theft techniques have evolved from simple phishing to sophisticated multi-stage operations that combine social engineering, technical exploitation, and psychological manipulation. Advanced persistent threats now conduct extensive reconnaissance before targeting specific individuals with access to critical systems, creating highly convincing scenarios designed to overcome security awareness training. These tailored approaches achieve significantly higher success rates than traditional broad-spectrum phishing attempts, even against security-conscious users.
The expanding use of workplace collaboration tools, messaging platforms, and mobile devices has created new vectors for credential theft attempts that bypass email security controls. Attackers increasingly leverage these alternative communication channels for initial contact, directing targets to convincing authentication pages or leveraging OAuth permissions to gain persistent access to accounts. The diversification of attack vectors creates substantial challenges for security teams attempting to monitor for compromise indicators across numerous communication platforms and application ecosystems.
MFA Bypass Techniques
While multi-factor authentication provides significant protection against credential theft, sophisticated attackers have developed various techniques to circumvent these controls. MFA fatigue attacks—which bombard users with authentication requests until they mistakenly approve one—have proven particularly effective against push-based authentication systems. Other bypass techniques include real-time phishing proxies that capture and replay authentication tokens, SIM swapping to intercept SMS verification codes, and social engineering tactics that trick users into providing MFA codes to attackers.
The security limitations of certain MFA implementations have become increasingly apparent, particularly those relying on SMS verification, phone calls, or basic push notifications. Organizations that implemented first-generation MFA solutions face increasing pressure to migrate to more phishing-resistant methods, including FIDO2 security keys, certificate-based authentication, and context-aware authentication systems that consider multiple risk factors beyond simple possession of a secondary device.
Digital Identity Fraud Trends
Beyond credential theft, sophisticated identity fraud techniques have emerged that exploit weaknesses in identity verification and authentication processes. Synthetic identity fraud—which combines legitimate and fabricated information to create new identities—has become particularly challenging to detect, especially in remote onboarding scenarios. These techniques allow attackers to establish seemingly legitimate accounts that pass standard verification checks while remaining under attacker control.
The increasing reliance on digital identity verification for remote access to financial services, healthcare, and government benefits has created high-value targets for sophisticated fraud operations. Organizations face the complex challenge of implementing sufficient identity verification to prevent fraud while maintaining acceptable user experiences and processing efficiency. This tension between security and usability creates persistent vulnerabilities in identity systems that attackers continuously evolve to exploit.
API Security Gaps Expose Critical Business Data

“Top 10 API Security Threats Every API …” from www.moesif.com and used with no modifications.
Application Programming Interfaces (APIs) have become the fundamental building blocks of modern digital ecosystems, enabling integration between services, data sharing between partners, and modular application architectures. However, this API-centric approach has created significant security challenges as organizations struggle to maintain visibility, access control, and security monitoring across rapidly expanding API landscapes. By 2026, API vulnerabilities have become the most common vector for data breaches, particularly in organizations with extensive digital transformation initiatives or microservice architectures.
Poorly Secured APIs as Attack Vectors
The rapid proliferation of APIs—often developed under aggressive timelines with primary focus on functionality rather than security—has created numerous security gaps that attackers systematically exploit. Common vulnerabilities include insufficient input validation, inadequate rate limiting, and overly permissive access controls that expose sensitive functionality or data. Many organizations lack comprehensive API inventories, resulting in “shadow APIs” that remain undocumented, unmonitored, and unprotected by API security tools.
The complexity of modern API ecosystems, which frequently span multiple development teams, technology stacks, and deployment environments, creates significant security governance challenges. Organizations struggle to implement consistent security standards across diverse API implementations, particularly when third-party and partner APIs are integrated into critical business processes. This inconsistency creates security weak points that sophisticated attackers specifically target after mapping API endpoints and analyzing response patterns for potential vulnerabilities.
API Authentication Weaknesses
Authentication weaknesses represent particularly critical vulnerabilities in API security, potentially allowing unauthorized access to sensitive data or functionality. Common issues include hardcoded credentials, insecure token handling, and excessive session durations that extend access beyond appropriate timeframes. Many organizations implement inconsistent authentication requirements across their API ecosystems, with internal or partner-facing APIs often receiving significantly less security scrutiny than public-facing interfaces.
The management of API keys, tokens, and secrets at scale has created significant operational challenges that frequently lead to security compromises. Secrets embedded in client-side code, stored in unprotected configuration files, or shared through insecure channels create persistent vulnerabilities that sophisticated attackers readily identify through automated scanning tools and code analysis. Even organizations with mature application security programs often struggle with the operational complexity of secure API credential management across development, testing, and production environments.
How to Defend Your Business Against 2026’s Cyber Threats
Defending against the sophisticated threats of 2026 requires a fundamental evolution in cybersecurity strategy, moving beyond perimeter-focused approaches to comprehensive security programs that emphasize resilience, detection capabilities, and response effectiveness. Organizations must adopt security architectures and operational practices that assume compromise will occur while implementing controls that limit attack spread, accelerate detection, and enable rapid response. This defense-in-depth approach, combined with specific technical countermeasures for emerging threats, provides the most effective protection against the complex threat landscape.
Implement Zero Trust Architecture Now
Zero Trust Architecture has evolved from theoretical concept to operational necessity, providing an effective framework for securing increasingly distributed and complex technology environments. This approach—which eliminates implicit trust, continuously validates every access request, and implements least-privilege access controls—provides substantial protection against credential theft, lateral movement, and data exfiltration attempts. Organizations should prioritize implementation of core Zero Trust principles, including strong authentication, micro-segmentation, and continuous monitoring and validation of all network transactions.
Use AI-Powered Security Tools
Artificial intelligence and machine learning have become essential components of effective security programs, enabling detection of subtle attack patterns, acceleration of response workflows, and automation of routine security tasks. These technologies help security teams manage the scale and complexity of modern threats by identifying anomalous behaviors that traditional rule-based systems would miss, reducing false positives through contextual analysis, and continuously adapting to evolving attack techniques. Organizations should implement AI-powered security monitoring across network, endpoint, identity, and application layers, while ensuring human oversight for critical security decisions.
Update Security Training for Modern Threats
Traditional security awareness training has proven insufficient against sophisticated social engineering attacks that leverage deepfakes, contextual information, and psychological manipulation techniques. Organizations must evolve their training approaches to emphasize critical thinking, verification procedures, and specific countermeasures for advanced social engineering tactics. This updated training should include realistic simulation exercises that reflect current attack techniques, role-specific security guidance for high-value targets like executives and IT administrators, and clear escalation paths for reporting suspicious activities.
For small businesses looking to enhance their security measures, exploring the best AI tools and software can be a valuable step.
Security culture development represents an equally important element of effective defense, creating organizational environments where security concerns are taken seriously and reporting suspicious activity is encouraged rather than discouraged. Organizations with strong security cultures show significantly higher resilience against social engineering attacks, as employees feel empowered to question unusual requests and follow verification procedures even under pressure. Leadership messaging, incentive structures, and operational practices should all reinforce the importance of security-conscious behavior throughout the organization.
Prepare for Post-Quantum Cryptography
Organizations must begin preparing for the quantum computing threat to cryptographic systems by implementing crypto-agility—the ability to rapidly transition between cryptographic algorithms without major system redesign. This preparation should include comprehensive cryptographic inventories to identify all systems using vulnerable algorithms, technical evaluations of post-quantum alternatives, and transition planning for critical systems. Organizations should prioritize systems with long-lived data protection requirements or those securing particularly sensitive information for early migration to quantum-resistant algorithms.
Conduct Regular Supply Chain Risk Assessments
Defending against supply chain attacks requires comprehensive visibility into third-party relationships, software dependencies, and hardware components throughout the technology ecosystem. Organizations should implement formal supply chain risk management programs that include vendor security assessments, software composition analysis, and hardware verification processes. These programs should establish clear security requirements for suppliers, implement continuous monitoring for supply chain compromises, and develop contingency plans for responding to third-party security incidents that impact critical dependencies.
Frequently Asked Questions
As organizations navigate the complex cybersecurity landscape of 2026, security leaders frequently raise questions about prioritization, resource allocation, and risk management approaches. These questions reflect the challenges of balancing security investments against competing business priorities while addressing rapidly evolving threats with limited resources and expertise.
The following responses address common questions about emerging cybersecurity threats and practical defense strategies for organizations of various sizes and technical capabilities.
What is the most dangerous cybersecurity threat expected in 2026?
While ransomware, nation-state attacks, and quantum computing threats all present significant risks, AI-powered attacks likely represent the most dangerous near-term threat for most organizations due to their accessibility, scalability, and effectiveness against current defense mechanisms. These attacks combine sophisticated techniques previously limited to advanced threat actors with automation capabilities that dramatically increase their reach and impact. Organizations should prioritize defenses specifically designed to counter AI-enhanced attacks, including AI-powered security monitoring, advanced phishing protection, and enhanced authentication systems resistant to automated compromise attempts.
That said, the most dangerous threat for any specific organization depends heavily on its industry, technical environment, and security maturity. Healthcare providers might face greater risk from ransomware targeting medical systems, while defense contractors might prioritize nation-state espionage threats. Effective risk assessment processes tailored to organizational context remain essential for appropriate threat prioritization.
For businesses looking to bolster their defenses, exploring the best AI tools can be a strategic move.
How can small businesses afford to protect against advanced AI-powered attacks?
Small businesses should focus on high-impact fundamentals that provide broad protection without requiring enterprise-scale security teams or budgets. These include implementing multi-factor authentication across all systems, maintaining comprehensive backup solutions with offline copies, using cloud-based security services that leverage AI for threat detection, and establishing basic security hygiene practices like prompt patching and minimal privilege models. Managed security service providers (MSSPs) offer increasingly affordable options for small businesses to access advanced security capabilities without maintaining in-house expertise.
Will cyber insurance policies change due to these emerging threats?
Cyber insurance markets have already begun significant evolution in response to escalating attack sophistication and frequency, with this trend accelerating through 2026. Insurers now require substantially more rigorous security controls as prerequisites for coverage, conduct detailed security assessments before issuing policies, and have implemented numerous exclusions for attacks resulting from inadequate security practices. Organizations should expect continued premium increases alongside more stringent security requirements, particularly for coverage related to ransomware, social engineering fraud, and supply chain compromises.
What industries are most at risk from these cybersecurity threats?
Critical infrastructure sectors—including healthcare, energy, financial services, and public utilities—face particularly high risk due to their operational impact and attractiveness as high-value targets. These sectors combine high willingness to pay ransoms (due to operational criticality) with often outdated technology stacks and complex regulatory environments that can slow security improvements. Technology companies also face elevated risk, particularly from intellectual property theft, supply chain attacks, and advanced persistent threats seeking access to their customer ecosystems.
How quickly should businesses implement quantum-resistant encryption?
Organizations should begin quantum-resistant encryption implementation planning immediately, with actual deployment prioritized based on data sensitivity and protection timeframes. Systems protecting information that must remain secure for 10+ years should receive highest priority, as this data faces risk from retrospective decryption once quantum capabilities mature. Most organizations should aim to complete transition of critical systems to quantum-resistant algorithms within 3-5 years while implementing crypto-agility across their environments to facilitate future transitions as standards evolve.
For businesses concerned about staying ahead of emerging cybersecurity threats, partnering with specialized security firms that focus on advanced threat detection and response capabilities can provide valuable expertise and technology resources.
Staying informed about evolving threats and implementing layered defenses remains the most effective approach to cybersecurity resilience in the increasingly complex digital landscape of 2026.


Join the Conversation